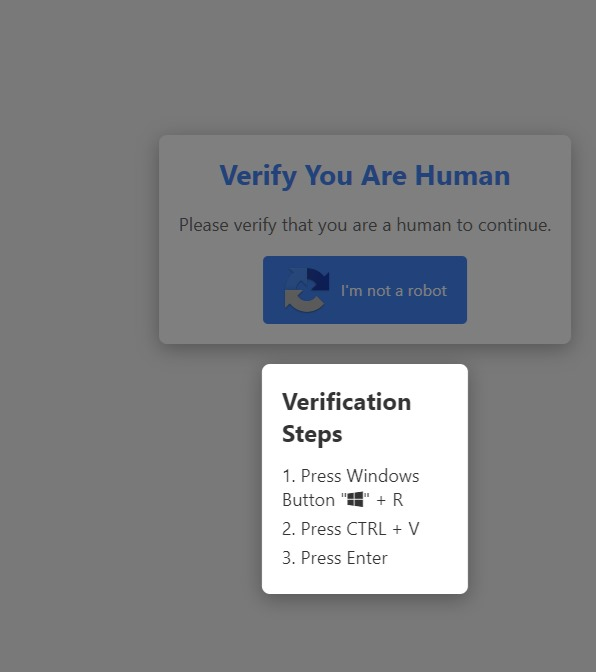
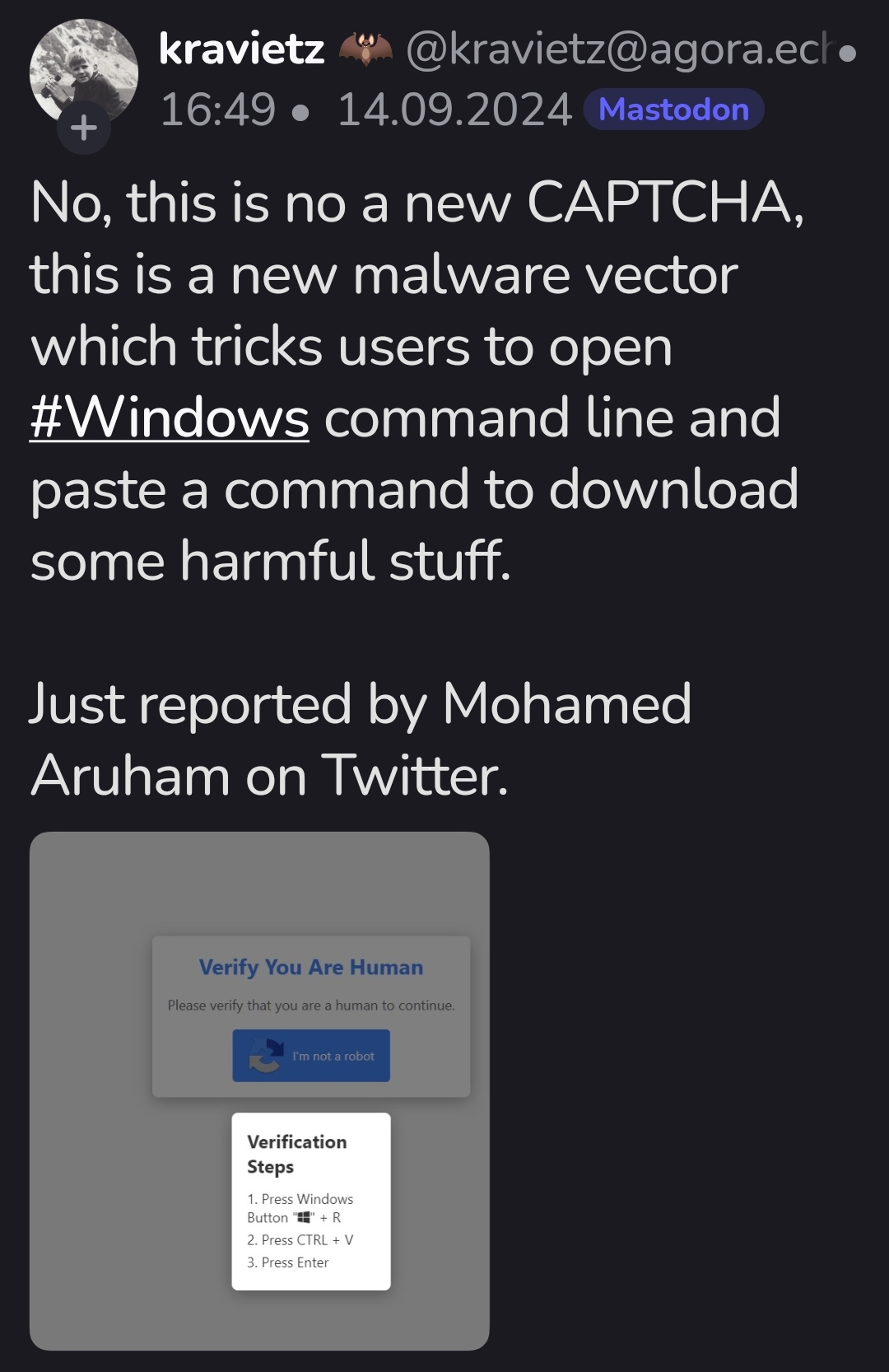
It seemed odd to me that a Web site could write to or read from the clipboard without the user approving it. That would be a pretty obvious security and privacy issue. From what I gather, on Chrome sites can write to the clipboard without approval, but they need approval to read. ~~On Firefox and others any access requires permission. Thus this exploit seems limited to Chrome users.~~
@SkaveRat pointed out that it doesn't require permission, only interaction. So likely there's a button that's clicked that writes to the clipboard, and most browsers are susceptible to this.